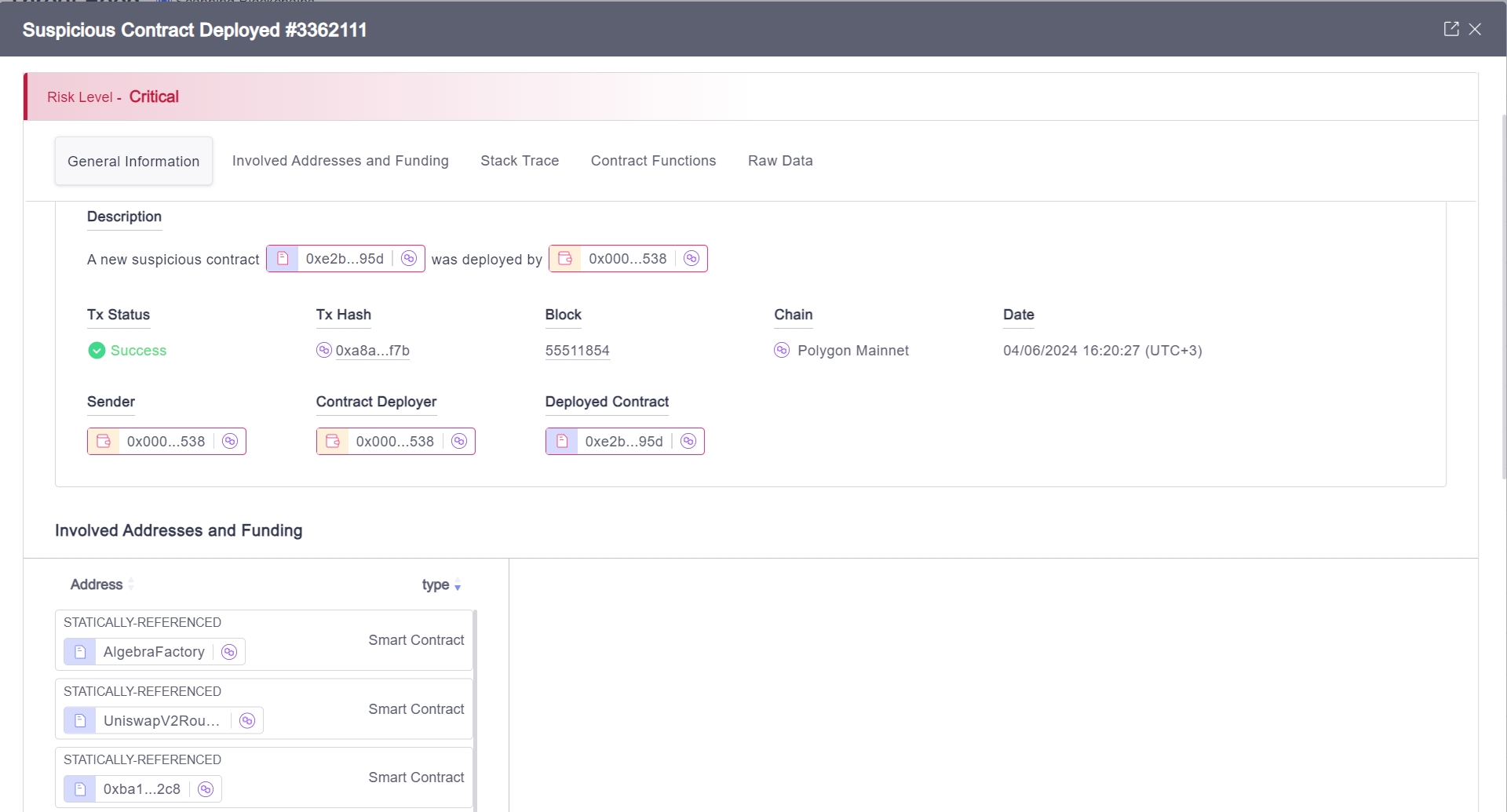
Suspicious Contract Deployed
Whenever a new contract is deployed on the blockchain, it undergoes a thorough analysis to detect any abnormalities in its bytecode, the authenticity of the deployer, simulations of its functions when applicable and other parameters that may indicate potential malicious activity. After this, the contract is flagged with a varying levels of severity and continuously monitored to prevent malicious activities.
We are continuously optimizing to detect threats upfront so we inspect any new contract that goes on-chain and combine it with many other signals we accumulate multi-chain such as malicious funding sources to take all of these together and compute a quality severity score so customers can act upon new suspicious contracts that we flagged as posing risk to the user monitored addresses.